World Of Warcraft Armory
Monday 4th January, 2010 13:18 Comments: 2
Be careful. Be very careful. Thankfully I haven't become a victim, but sadly Cheryl was the other day. She was lucky that no one added an authenticator to her account or stole her characters' items, but they did steal all the gold from her main account (although she didn't have that much).
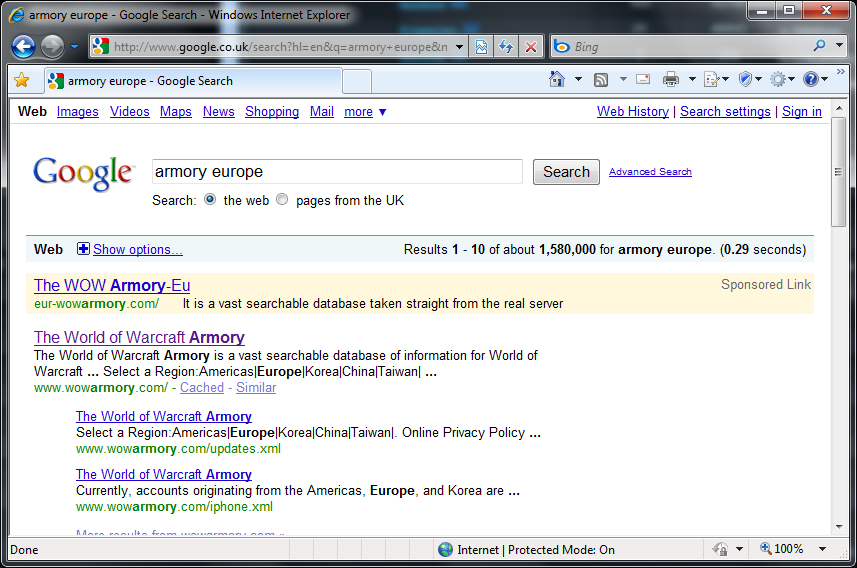
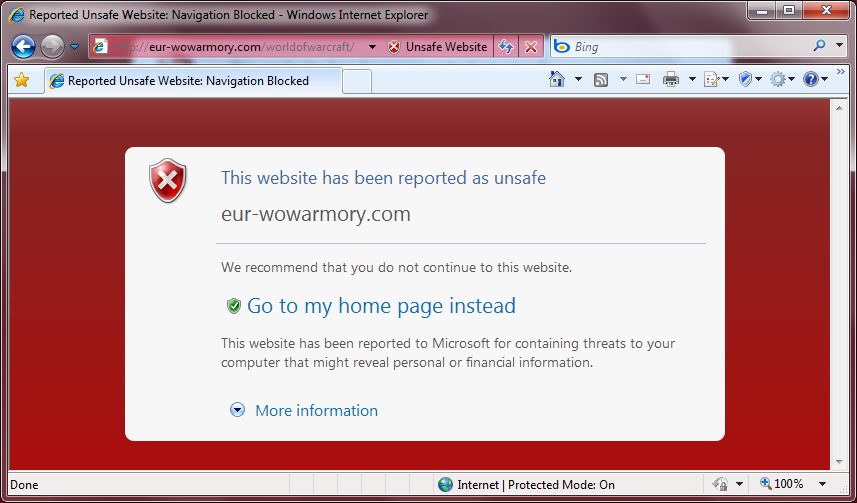
Thankfully IE's SmartScreen Filter seems to spot them after a while (for some reason it didn't spot it on Cheryl's main PC, even though mine and the PC downstairs did :-S), and Google has presumably removed some of the adwords as it keeps coming back with a different folder, and more recently has changed domain name to one that's easier to spot as a fake (armory-worldofwarcrafe.com - seriously?). I've been reporting the AdWords to Google and the sites to Microsoft and hopefully that's helping people.
The site itself is pretty clever. It loads CSS files directly from the official site (eu.battle.net), it looks like the real site (probably a copy and paste of the code), but there are a few obvious flaws. The links to different languages (and other links across the page) don't take you anywhere. No matter where you try and go, all the other links take you to a static login page. This is where it gets clever though, as the form is submitted to the real server. What they appear to have done is changed the onsubmit code so it runs a local JavaScript function. I had a quick look, but the code is partially obfuscated (nothing an unpacker couldn't decode, I'm sure), and I suspect all it does is capture the username and password and (perhaps depending on the response from the server) sends it to the phishers.


Thankfully IE's SmartScreen Filter seems to spot them after a while (for some reason it didn't spot it on Cheryl's main PC, even though mine and the PC downstairs did :-S), and Google has presumably removed some of the adwords as it keeps coming back with a different folder, and more recently has changed domain name to one that's easier to spot as a fake (armory-worldofwarcrafe.com - seriously?). I've been reporting the AdWords to Google and the sites to Microsoft and hopefully that's helping people.
The site itself is pretty clever. It loads CSS files directly from the official site (eu.battle.net), it looks like the real site (probably a copy and paste of the code), but there are a few obvious flaws. The links to different languages (and other links across the page) don't take you anywhere. No matter where you try and go, all the other links take you to a static login page. This is where it gets clever though, as the form is submitted to the real server. What they appear to have done is changed the onsubmit code so it runs a local JavaScript function. I had a quick look, but the code is partially obfuscated (nothing an unpacker couldn't decode, I'm sure), and I suspect all it does is capture the username and password and (perhaps depending on the response from the server) sends it to the phishers.
You can add armory-woldofwarcraft.com to the list too. Registered by someone in China, and running what appears to be a Chinese version of IIS. I've reported it to Google and Microsoft. It appears to be the same server each time (174.139.6.180), hosted by Krypt Technologies.
They keep changing the directory (and Google's sponsored link), so I'm giving up. I've reported it to Microsoft and to Google (again), but I've now blocked the IP range - on my router - that's used by the phishing site. That should stop me from getting to their site ever again.