Privacy
Saturday 5th May, 2007 14:12 Comments: 0
I was reading an article on The Register (one that felt incredibly dated, with its references to 2000 and XP - and is probably a rehash of a much older article) and was getting a bit annoyed with it. Then I noticed who had written it. Anyway, I'll try and keep this short, but the article makes the following points:
For example, if you were hoping to boot off a Linux Live CD and gain access to the files, you need the BIOS to be configured to boot off the CD before the hard disk. Ideally a BIOS password will also have been set, so you can't change the default setting, and the option to access the boot selection menu should have been disabled.
Otherwise, you need to unscrew the case and pull the hard disk out and attach it to another system. You can buy cases with a basic locking mechanism, which would put off most people, and/or attach a nice Kensington lock so it suddenly becomes a lot harder to access that hard disk.
The attacker also has to gain physical access to the computer, which means either they broke into your house (specifically to steal you hard disk?) or you invited them in (and then left them alone in your house for an extended period of time).
If a user really has access to the drive or system, there are easier ways to gain entry. If Remote Desktop is enabled and the user has a password, you could try and bruteforce your way in (less likely to lock the account, assuming the user even bothered with an account lockout policy) - this could even be done over the internet without the user realising/you having to steal the computer. You could perhaps steal the system and wait a few months until a nice vulnerability is discovered and use that to gain access (assuming that the system isn't left connected to the internet and automatically installing patches from Windows Update). You could use a tool to disable SYSKEY on the disk and then blank out or set a new password (not 100% reliable) for the user.
Or you could stick with the typical methods, such as targeted malicious documents that silently install trojan software. It might not be as reliable, but it's probaby a hell of a lot easier than breaking into a house to steal a hard disk.
Either way, these "privacy" measures of encrypting/wiping pagefile.sys and hiberfil.sys are mostly a waste of time (there are typically easier ways to gain access to the same data) and will affect the performance of your computer (hint: not in a positive way).
* Windows Vista can encrypt the page file, eliminating the need to set the "clear virtual memory pagefile" option. The entire design of Offline Files has been reworked in Windows Vista. In addition to much better performance and stability (as well as a generally more user-friendly interface), client-side caching is now per user, meaning it is possible to securely encrypt the cache without the use of SYSKEY mode 2 or 3. Windows Vista also allows administrators to configure encryption of the Documents folder directly through Group Policy, without having to utilize a separate script. The image below illustrates the new EFS properties available via GPO in Windows Vista.
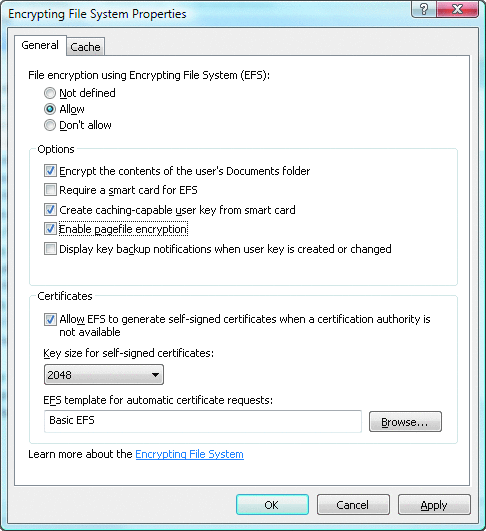
- The files pagefile.sys and hiberfil.sys are unencrypted on the hard disk for Windows 2000 and XP users
- Tools that encrypt these files cost money for Windows 2000 and XP users
- Linux users can use free tools to encryt/securely wipe their swap file, and Linux doesn't typically support hibernation
For example, if you were hoping to boot off a Linux Live CD and gain access to the files, you need the BIOS to be configured to boot off the CD before the hard disk. Ideally a BIOS password will also have been set, so you can't change the default setting, and the option to access the boot selection menu should have been disabled.
Otherwise, you need to unscrew the case and pull the hard disk out and attach it to another system. You can buy cases with a basic locking mechanism, which would put off most people, and/or attach a nice Kensington lock so it suddenly becomes a lot harder to access that hard disk.
The attacker also has to gain physical access to the computer, which means either they broke into your house (specifically to steal you hard disk?) or you invited them in (and then left them alone in your house for an extended period of time).
If a user really has access to the drive or system, there are easier ways to gain entry. If Remote Desktop is enabled and the user has a password, you could try and bruteforce your way in (less likely to lock the account, assuming the user even bothered with an account lockout policy) - this could even be done over the internet without the user realising/you having to steal the computer. You could perhaps steal the system and wait a few months until a nice vulnerability is discovered and use that to gain access (assuming that the system isn't left connected to the internet and automatically installing patches from Windows Update). You could use a tool to disable SYSKEY on the disk and then blank out or set a new password (not 100% reliable) for the user.
Or you could stick with the typical methods, such as targeted malicious documents that silently install trojan software. It might not be as reliable, but it's probaby a hell of a lot easier than breaking into a house to steal a hard disk.
Either way, these "privacy" measures of encrypting/wiping pagefile.sys and hiberfil.sys are mostly a waste of time (there are typically easier ways to gain access to the same data) and will affect the performance of your computer (hint: not in a positive way).
* Windows Vista can encrypt the page file, eliminating the need to set the "clear virtual memory pagefile" option. The entire design of Offline Files has been reworked in Windows Vista. In addition to much better performance and stability (as well as a generally more user-friendly interface), client-side caching is now per user, meaning it is possible to securely encrypt the cache without the use of SYSKEY mode 2 or 3. Windows Vista also allows administrators to configure encryption of the Documents folder directly through Group Policy, without having to utilize a separate script. The image below illustrates the new EFS properties available via GPO in Windows Vista.
