Vista Security Overview
Wednesday 21st February, 2007 11:17 Comments: 2
Well I did warn the Editor of The Register the other day, but it seems he still published Thomas C Greene's article on his security and privacy concerns in Vista. As I predicted, it was the same poor quality as Greene's last articles.
In a nutshell, Windows is single-handedly responsible for turning the internet into the toxic shithole of malware that it is today.
I think that's a bit harsh. The majority of problems are caused by users. Users choose to run as Admin, install malware-infested software, but don't bother installing security patches. Windows XP SP2 introduced an improved firewall that was on by default, and since then the number of large remote attacks have basically dropped to 0. You still get the odd remote attack coming in via things like email, but they typically require user interaction (with the notable exception of a recent Outlook one).
This doesn't perhaps sound like a huge improvement, but when you look at data from McAfee Avert Labs it's clear that the number of days for a worm to appear after a patch was available has dropped from a staggering 335 day (Nimda, one of the most annoying viruses, which would have been stopped if users installed updates on more than a yearly basis) to just 4 days (Mocbot). The malware authors are getting quicker and their malware is often harder to detect, yet the internet still works. Estimates seem to suggest that 10-25% of machines on the internet are infected. In some cases (especially recent ones) that means that malware is installed, but some malware has been known to patch the vulnerability and even install a pirated version of Kaspersky in order to protect itself from being removed by another piece of malware! For the record, don't blame pirate users either, they could still get security updates for Windows XP. In fact, during 2006, over 50% of viruses reported to Sophos were either W32/Mytob or W32/Netsky, which date back to March 2005 and March 2004 respectively! Mytob, at a fraction under 30%, is spread via email attachments, so you have to blame the user!
That's not going to change any time soon, no matter how good Vista's security might be
Although many people criticise Vista for forcing many users to perform a clean install, this is usually good for several reasons. Your system won't bring any problems across (i.e. malware), and begins with a clean slate with all the correct default settings. As more people adopt Vista, the harder it'll be to infect users, especially with an improved firewall. The only reason why things might not change soon is because of the FUD (fear, uncertainty and doubt) surrounding Vista. Articles such as Greene's clearly don't encourage users to jump.
However, IE7 on Vista does still write to parts of the registry in protected mode. And it appears to write to parts that MS says is won't. The company says that "a low integrity process, such as Internet Explorer in Protected Mode, can create and modify files in low integrity folders". We are assured that such low integrity processes "cannot gain write access to objects at higher integrity levels". And again, MS emphasises that a low integrity process "can only write to low integrity locations, such as the Temporary Internet Files\\Low folder or the HKEY_CURRENT_USER\\Software\\LowRegistry key".
So I tested this assurance. I ran IE in protected mode, typed a URL into the location bar and went there. Then I opened regedit, and searched for a string of text from that URL.
Sadly, IE7 is still stashing typed URLs in the registry, and not in the ...\\LowRegistry location, either. I found them in HKEY_CURRENT_USER\\Software\\Microsoft\\Internet Explorer\\TypedURLs
Guess what, there are other things like the "Default HTML Editor" and "Main" (which covers settings such as Display Inline Images and Friendly http errors). These are all settings that are held by the browser. If you use Process Explorer you can see that iexplore.exe and ieuser.exe are both running. If you use Google you can discover fairly quickly (the same article that Greene linked to, but obviously didn't bother reading), which says: "Two higher privilege broker processes allow Internet Explorer and extensions to perform elevated operations given user consent. For example, the user privilege broker (IEUser.exe) process provides a set of functions that let the user saves files to areas outside of low integrity areas. In addition, an administrator privilege broker (IEInstal.exe) process allows Internet Explorer to install ActiveX controls."
That means that a certain subset of functions (such as settings in IE, typed URLs) that pose no security risk are allowed access to other areas. That page also lists other useful info, such as how "extensions can not write to system locations such as the Program Files folder or the HKEY_CLASSES_ROOT or HKEY_LOCAL_MACHINE subtrees" and that Access Denied is returned when extensions try and access certain files used by IE and Vista.
Next, there is IE7's anti-phishing filter gimmick. I disabled it almost immediately. It's very showy and it says, "Message: We Care", but I found it more irritating than actually helpful. I think a lot of users will disable it, and trust their instincts instead.
Just because you disabled it doesn't meant that everyone else will. First he tries to disable the Security Center in Vista, now he's trying to turn off the phishing filter, one which has performed very well (PDF) in independent (PDF) tests (PDF) and are clearly better than the small minority of users that use their instincts and fail to spot phishing sites. Sadly, that small minority that clearly can't be trusted to make the right decision still makes it cost effective to send phishing emails and construct phishing sites. The latter PDF I linked to suggested that Firefox performed better than IE7, but IE7 hasn't suffered from the same (numerous) vulnerabilities in the Firefox's filter (adding an additional forward slash at the end of the domain name, changing the query string at the end of the URL) or privacy concerns (when Google left a bunch of data on their server for anyone to see).
IE7 also has a handy menu for deleting your history, cookies, cache, and so on. This is similar to the Mickey Mouse privacy utility in Firefox. Remember that these data traces are not securely wiped, but merely deleted. They remain on your HDD until they happen to be overwritten. Firefox will let you delete all that stuff automatically each time you exit; IE won't
Vista also doesn't have a method of securely deleting files that have been deleted, so it's no surprise that it doesn't securely delete your data. And cookies are hardly the dangerous malware that many products like to claim. I don't particularly care about my history, cookies, cache and so on being visible to anyone that logs onto my computer as me. Possibly because I don't visit any dodgy sounding websites. His point about defaults like saving third party cookies is valid, but he also suggests "disabling MetaRefresh" - doing so can be more irritating than IE7's phishing filter! Many websites assume the meta tag will work and don't provide a link to the next page. I can't remember the last time I saw someone use a meta refresh tag to do something malicious. And there are other ways to redirect users (Location header, perhaps done using CRLF header injection), along with other methods of attack (DNS poisoning, APR spoofing, MITM attacks).
The privacy conscious are, as always, encouraged to use Mozilla for browsing instead
Yes, although Google's phishing filter has resulted in private data (passwords) being leaked. And the Firefox filter has been trivially bypassed in the past ("When Phishing Protection is used in default mode, no information about the sites you visit is sent to Mozilla or anti-phishing partners. Rather, sites are checked against a local list that is downloaded to your computer and updated on a regular basis" - although perhaps not regularly enough). Plus Firefox does have a few flaws too.
Now, with IE7, such links show up in the status bar as the full URL when you mouse over them, but in Windows Mail they don't. This should be fixed, because otherwise one is stuck relying solely on Microsoft's anti-phishing filter gimmick
When you hover over URLs in Windows Mail or Outlook 2007, the real URL appears as a tooltip. I don't use Windows Mail as my mail client, but if I save a draft email I can see the real URL stated in the status bar. I haven't tried any fancy JavaScript tricks to change the visible URL, but that doesn't work in IE7 as you can't write messages to the status bar anymore. I can't really see what needs to be "fixed".
Data Execution Prevention (DEP) is a feature from XP SP2 that shuts down programs that handle memory oddly, and it is now set to full on by default. It works with address space layout randomisation, a new feature in Vista that loads some system code in unpredictable memory locations to defend against buffer overflow attacks. Both are very good ideas, and should help reduce the impact of malware to some extent.
One of the biggest things in Vista is it's improved handling of programs that don't use memory properly. And he covers it in one pararaph. At least he mentioned the words ASLR, with a quick and dirty explanation.
However, DEP, when full on, may cause a number of applications to crash, or interfere with their installation. I'm betting that a majority of users will opt for the more conservative setting, and this of course means less defense for everyone.
The only programs that crashed when I had DEP enabled for everything on Vista x64 were:
wow.exe (World of Warcraft)
msfeedsync.exe (Microsoft RSS feed synchronization)
The latter DEP error was caused by NOD32, and uninstalling it and using alternate AV software made the problem go away. I never did double check whether new builds of wow.exe fixed the problem (there have been a lot of patches recently). Other than those issues, I've had no problems with DEP, and nor will other users. I doubt that the majority will disable it. If they do, it's probably because they're using legacy applications. Find an alternative, don't disable DEP!
User Account Control (UAC) is another good idea, because it finally, finally, finally allows the machine's owner to work from a standard user account, and still perform administrative tasks by supplying admin credentials as needed on a per-action basis. You know, the way Linux has been doing it forever.
You could always do that, using "runas", Vista simply makes it prettier and simpler. There are a few subtle differences, but not usually enough to affect users. Well written applications don't typically need privilege escalation. Even QuickBooks 2007 finally works as a standard user (much to the relief of many people I know)
MS still encourages the person who installs Vista (the owner presumably) to run their machine with admin privileges by default. I was delighted, when I set up Vista for the first time, to be presented with an opportunity to set up a "user" account. But moments later, when I saw that I was not invited also to create an admin account, I knew that the "user" account I had just set up was indeed an admin account. And so it was.
If only he'd tried creating a second account.
Until MS gets it through their thick skulls that a multi-user OS needs a separate admin account and a user account for the owner, and that the owner should be encouraged to work from a regular user account as much as possible, UAC will never work as intended.
Until Greene gets it through his thick skull that he's a poor journalist, we shall suffer an almost-endless amount of FUD. Here's what really happens when you create users in Vista:
The first user you create is an Admin user.
If there is an Admin user in addition to the default (500) Administrator account, Vista will disable the Administrator account. You cannot log on locally or remotely with this account until all other Admin accounts have been removed.
All additional users are created - by default - as "Standard user".
On this system I have my account, Guest (off) and here I am about to try and add a new user:
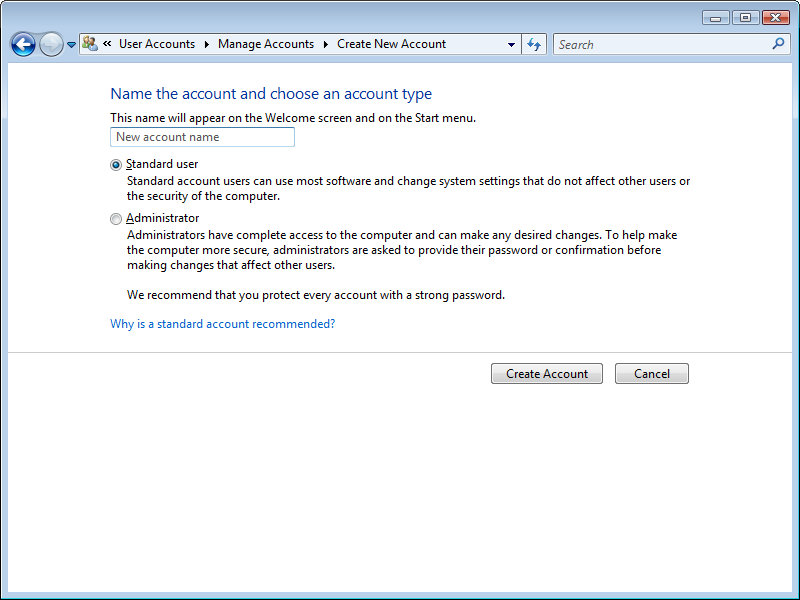
Doesn't sound so terrible to me, this is more secure than previous versions of Windows, and by disabling all the default accounts, attackers will need to try and brute force the username and password, not just the password for default accounts.
In fact, UAC is the most complained-about new feature of Vista, and most people are disabling it as soon as possible.
Where are the facts, statistics, surveys, studies, evidence to back this up? I don't see any. Maybe it was a straw poll of the office. Maybe he just made it up. Who knows.
One should definitely not hide file extensions, as the default file view has it, because it is possible to spoof icons and use bogus extensions that can make executables appear to be other than they are. Yes, UAC and DEP are supposed to help with this, but DEP will be set to its lower setting, and UAC will be turned off, on the vast majority of Vista boxes, for reasons we've already discussed.
I agree that file extensions should be visible (I turn them back on), but something needs to get a file onto your computer in the first place. If they can already do this then it's probably game over. Files that enter Vista are checked using the Attachment Execution Service API, which will block anything that can be executed. If my JPEG image asks if I want to unblock it before running it, the alarm bell in my head should already be ringing.
As usual, Windows enables far too many services by default
Such as? To be honest, I can't see many services I'd disable if I were trying to lock down Vista, and most of them I'd leave so that programs will play nicely (e.g. Portable Device Enumerator Service). This is coming from me, someone that sometimes performs server hardening as part of their job.
It would be a tremendous help if MS could somehow use its many wizards to enable only the services needed for each bit of hardware or software installed
Well I only see the Infrared monitor service on my laptop, I don't remember seeing it on my desktop.
But with this new gimmick, you've got an archive of all the files you've looked at, regardless of where you've buried them in the file system hierarchy in hopes of keeping prying eyes off them, and you can't empty it unless you want to say goodbye to the files themselves.
Guess what, you can only see that Recently Changed folder when you're logged on. I think all privacy concerns go out of the window when another user has access to your account. I used to find it very annoying when Windows' search would find the shortcuts in the Recent Documents folder, especially when I used TweakUI to remove the shortcut icon.
Now, for the Vista Security Centre. This has been controversial, involving MS in skirmishes with security software vendors who claim that Vista's built-in product is anti-competitive.
I'm not sure why anyone would worry
Wait a second, isn't that the same person that wrote a few days ago that it was something he tried to disable? He even called it a "craplet". For reference, you need to "Change the way Security Center alerts me" first before you turn off/disable the Security Center service, if you don't want the little red shield icon to bug you when Security Center is disabled. I do not personally condone this action, I would much rather see users keep Security Center enabled, notifying them and displaying an icon (the top option).
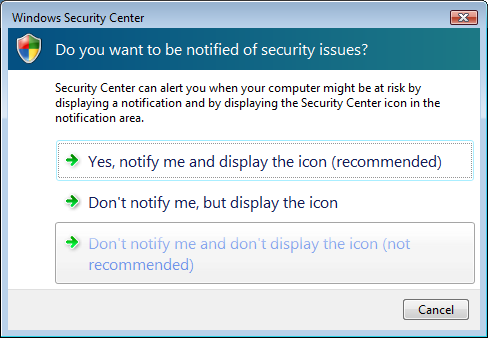
I noticed one exception in the default firewall configuration that I didn't care for, for allowing remote assistance. I don't think that should be allowed unless you're actually using remote assistance.
I do kind of agree with that, but normally you only use Remote Assistance with users that aren't clever enough to follow your instructions, which usually rules out asking them to modify their firewall so you can take over. In a corporate environment, you'd probably disable that firewall rule and use commercial software (with its own rules) instead to take control.
I certainly wouldn't recommend depending solely on Windows Defender. But it's nice that it's there.
I think that's why it was left in, as people would otherwise question why it's removed, even though it's not perfect, and there are so many reasons why Vista ought to stop something getting onto the user's system anyway. It's like the Malicious Software Removal Tool that Microsoft periodically updates and puts on Windows Update, it's not perfect, it's probably too late, but it makes people happy.
MS has, in a sense, shifted the responsibility onto users
Perhaps that's because they're the problem. Stick an IIS6 box on the web with just port 80 open, and assuming you're only serving static pages (ASP is off by default), that box will never have been compromised between then and now (unless someone knows of an 0-day that I'm not aware of?). Even if you didn't bother installing any patches. Even if you installed ASP, unless someone could upload files to the server and make IIS execute them, you're still not compromised (unless you do something really dodgy in your web application, which typically involves weakening lots of default settings). As a standalone system, Windows is perfectly fine. Once you start putting it on a network, allowing RPC ports to be opened up, exceptions for third party software, using a browser (any browser), that's when the problems start.
Correction I'm grateful to a Reg reader who pointed out an error in a previous edition of this story. I had stated incorrectly that IE7 doesn't allow blocking third-party cookies. It defaults to accepting them, but can be made to block them.
Greene's articles generally need a lot of correcting. Especially his recent ones.
In a nutshell, Windows is single-handedly responsible for turning the internet into the toxic shithole of malware that it is today.
I think that's a bit harsh. The majority of problems are caused by users. Users choose to run as Admin, install malware-infested software, but don't bother installing security patches. Windows XP SP2 introduced an improved firewall that was on by default, and since then the number of large remote attacks have basically dropped to 0. You still get the odd remote attack coming in via things like email, but they typically require user interaction (with the notable exception of a recent Outlook one).
This doesn't perhaps sound like a huge improvement, but when you look at data from McAfee Avert Labs it's clear that the number of days for a worm to appear after a patch was available has dropped from a staggering 335 day (Nimda, one of the most annoying viruses, which would have been stopped if users installed updates on more than a yearly basis) to just 4 days (Mocbot). The malware authors are getting quicker and their malware is often harder to detect, yet the internet still works. Estimates seem to suggest that 10-25% of machines on the internet are infected. In some cases (especially recent ones) that means that malware is installed, but some malware has been known to patch the vulnerability and even install a pirated version of Kaspersky in order to protect itself from being removed by another piece of malware! For the record, don't blame pirate users either, they could still get security updates for Windows XP. In fact, during 2006, over 50% of viruses reported to Sophos were either W32/Mytob or W32/Netsky, which date back to March 2005 and March 2004 respectively! Mytob, at a fraction under 30%, is spread via email attachments, so you have to blame the user!
That's not going to change any time soon, no matter how good Vista's security might be
Although many people criticise Vista for forcing many users to perform a clean install, this is usually good for several reasons. Your system won't bring any problems across (i.e. malware), and begins with a clean slate with all the correct default settings. As more people adopt Vista, the harder it'll be to infect users, especially with an improved firewall. The only reason why things might not change soon is because of the FUD (fear, uncertainty and doubt) surrounding Vista. Articles such as Greene's clearly don't encourage users to jump.
However, IE7 on Vista does still write to parts of the registry in protected mode. And it appears to write to parts that MS says is won't. The company says that "a low integrity process, such as Internet Explorer in Protected Mode, can create and modify files in low integrity folders". We are assured that such low integrity processes "cannot gain write access to objects at higher integrity levels". And again, MS emphasises that a low integrity process "can only write to low integrity locations, such as the Temporary Internet Files\\Low folder or the HKEY_CURRENT_USER\\Software\\LowRegistry key".
So I tested this assurance. I ran IE in protected mode, typed a URL into the location bar and went there. Then I opened regedit, and searched for a string of text from that URL.
Sadly, IE7 is still stashing typed URLs in the registry, and not in the ...\\LowRegistry location, either. I found them in HKEY_CURRENT_USER\\Software\\Microsoft\\Internet Explorer\\TypedURLs
Guess what, there are other things like the "Default HTML Editor" and "Main" (which covers settings such as Display Inline Images and Friendly http errors). These are all settings that are held by the browser. If you use Process Explorer you can see that iexplore.exe and ieuser.exe are both running. If you use Google you can discover fairly quickly (the same article that Greene linked to, but obviously didn't bother reading), which says: "Two higher privilege broker processes allow Internet Explorer and extensions to perform elevated operations given user consent. For example, the user privilege broker (IEUser.exe) process provides a set of functions that let the user saves files to areas outside of low integrity areas. In addition, an administrator privilege broker (IEInstal.exe) process allows Internet Explorer to install ActiveX controls."
That means that a certain subset of functions (such as settings in IE, typed URLs) that pose no security risk are allowed access to other areas. That page also lists other useful info, such as how "extensions can not write to system locations such as the Program Files folder or the HKEY_CLASSES_ROOT or HKEY_LOCAL_MACHINE subtrees" and that Access Denied is returned when extensions try and access certain files used by IE and Vista.
Next, there is IE7's anti-phishing filter gimmick. I disabled it almost immediately. It's very showy and it says, "Message: We Care", but I found it more irritating than actually helpful. I think a lot of users will disable it, and trust their instincts instead.
Just because you disabled it doesn't meant that everyone else will. First he tries to disable the Security Center in Vista, now he's trying to turn off the phishing filter, one which has performed very well (PDF) in independent (PDF) tests (PDF) and are clearly better than the small minority of users that use their instincts and fail to spot phishing sites. Sadly, that small minority that clearly can't be trusted to make the right decision still makes it cost effective to send phishing emails and construct phishing sites. The latter PDF I linked to suggested that Firefox performed better than IE7, but IE7 hasn't suffered from the same (numerous) vulnerabilities in the Firefox's filter (adding an additional forward slash at the end of the domain name, changing the query string at the end of the URL) or privacy concerns (when Google left a bunch of data on their server for anyone to see).
IE7 also has a handy menu for deleting your history, cookies, cache, and so on. This is similar to the Mickey Mouse privacy utility in Firefox. Remember that these data traces are not securely wiped, but merely deleted. They remain on your HDD until they happen to be overwritten. Firefox will let you delete all that stuff automatically each time you exit; IE won't
Vista also doesn't have a method of securely deleting files that have been deleted, so it's no surprise that it doesn't securely delete your data. And cookies are hardly the dangerous malware that many products like to claim. I don't particularly care about my history, cookies, cache and so on being visible to anyone that logs onto my computer as me. Possibly because I don't visit any dodgy sounding websites. His point about defaults like saving third party cookies is valid, but he also suggests "disabling MetaRefresh" - doing so can be more irritating than IE7's phishing filter! Many websites assume the meta tag will work and don't provide a link to the next page. I can't remember the last time I saw someone use a meta refresh tag to do something malicious. And there are other ways to redirect users (Location header, perhaps done using CRLF header injection), along with other methods of attack (DNS poisoning, APR spoofing, MITM attacks).
The privacy conscious are, as always, encouraged to use Mozilla for browsing instead
Yes, although Google's phishing filter has resulted in private data (passwords) being leaked. And the Firefox filter has been trivially bypassed in the past ("When Phishing Protection is used in default mode, no information about the sites you visit is sent to Mozilla or anti-phishing partners. Rather, sites are checked against a local list that is downloaded to your computer and updated on a regular basis" - although perhaps not regularly enough). Plus Firefox does have a few flaws too.
Now, with IE7, such links show up in the status bar as the full URL when you mouse over them, but in Windows Mail they don't. This should be fixed, because otherwise one is stuck relying solely on Microsoft's anti-phishing filter gimmick
When you hover over URLs in Windows Mail or Outlook 2007, the real URL appears as a tooltip. I don't use Windows Mail as my mail client, but if I save a draft email I can see the real URL stated in the status bar. I haven't tried any fancy JavaScript tricks to change the visible URL, but that doesn't work in IE7 as you can't write messages to the status bar anymore. I can't really see what needs to be "fixed".
Data Execution Prevention (DEP) is a feature from XP SP2 that shuts down programs that handle memory oddly, and it is now set to full on by default. It works with address space layout randomisation, a new feature in Vista that loads some system code in unpredictable memory locations to defend against buffer overflow attacks. Both are very good ideas, and should help reduce the impact of malware to some extent.
One of the biggest things in Vista is it's improved handling of programs that don't use memory properly. And he covers it in one pararaph. At least he mentioned the words ASLR, with a quick and dirty explanation.
However, DEP, when full on, may cause a number of applications to crash, or interfere with their installation. I'm betting that a majority of users will opt for the more conservative setting, and this of course means less defense for everyone.
The only programs that crashed when I had DEP enabled for everything on Vista x64 were:
wow.exe (World of Warcraft)
msfeedsync.exe (Microsoft RSS feed synchronization)
The latter DEP error was caused by NOD32, and uninstalling it and using alternate AV software made the problem go away. I never did double check whether new builds of wow.exe fixed the problem (there have been a lot of patches recently). Other than those issues, I've had no problems with DEP, and nor will other users. I doubt that the majority will disable it. If they do, it's probably because they're using legacy applications. Find an alternative, don't disable DEP!
User Account Control (UAC) is another good idea, because it finally, finally, finally allows the machine's owner to work from a standard user account, and still perform administrative tasks by supplying admin credentials as needed on a per-action basis. You know, the way Linux has been doing it forever.
You could always do that, using "runas", Vista simply makes it prettier and simpler. There are a few subtle differences, but not usually enough to affect users. Well written applications don't typically need privilege escalation. Even QuickBooks 2007 finally works as a standard user (much to the relief of many people I know)
MS still encourages the person who installs Vista (the owner presumably) to run their machine with admin privileges by default. I was delighted, when I set up Vista for the first time, to be presented with an opportunity to set up a "user" account. But moments later, when I saw that I was not invited also to create an admin account, I knew that the "user" account I had just set up was indeed an admin account. And so it was.
If only he'd tried creating a second account.
Until MS gets it through their thick skulls that a multi-user OS needs a separate admin account and a user account for the owner, and that the owner should be encouraged to work from a regular user account as much as possible, UAC will never work as intended.
Until Greene gets it through his thick skull that he's a poor journalist, we shall suffer an almost-endless amount of FUD. Here's what really happens when you create users in Vista:
The first user you create is an Admin user.
If there is an Admin user in addition to the default (500) Administrator account, Vista will disable the Administrator account. You cannot log on locally or remotely with this account until all other Admin accounts have been removed.
All additional users are created - by default - as "Standard user".
On this system I have my account, Guest (off) and here I am about to try and add a new user:

Doesn't sound so terrible to me, this is more secure than previous versions of Windows, and by disabling all the default accounts, attackers will need to try and brute force the username and password, not just the password for default accounts.
In fact, UAC is the most complained-about new feature of Vista, and most people are disabling it as soon as possible.
Where are the facts, statistics, surveys, studies, evidence to back this up? I don't see any. Maybe it was a straw poll of the office. Maybe he just made it up. Who knows.
One should definitely not hide file extensions, as the default file view has it, because it is possible to spoof icons and use bogus extensions that can make executables appear to be other than they are. Yes, UAC and DEP are supposed to help with this, but DEP will be set to its lower setting, and UAC will be turned off, on the vast majority of Vista boxes, for reasons we've already discussed.
I agree that file extensions should be visible (I turn them back on), but something needs to get a file onto your computer in the first place. If they can already do this then it's probably game over. Files that enter Vista are checked using the Attachment Execution Service API, which will block anything that can be executed. If my JPEG image asks if I want to unblock it before running it, the alarm bell in my head should already be ringing.
As usual, Windows enables far too many services by default
Such as? To be honest, I can't see many services I'd disable if I were trying to lock down Vista, and most of them I'd leave so that programs will play nicely (e.g. Portable Device Enumerator Service). This is coming from me, someone that sometimes performs server hardening as part of their job.
It would be a tremendous help if MS could somehow use its many wizards to enable only the services needed for each bit of hardware or software installed
Well I only see the Infrared monitor service on my laptop, I don't remember seeing it on my desktop.
But with this new gimmick, you've got an archive of all the files you've looked at, regardless of where you've buried them in the file system hierarchy in hopes of keeping prying eyes off them, and you can't empty it unless you want to say goodbye to the files themselves.
Guess what, you can only see that Recently Changed folder when you're logged on. I think all privacy concerns go out of the window when another user has access to your account. I used to find it very annoying when Windows' search would find the shortcuts in the Recent Documents folder, especially when I used TweakUI to remove the shortcut icon.
Now, for the Vista Security Centre. This has been controversial, involving MS in skirmishes with security software vendors who claim that Vista's built-in product is anti-competitive.
I'm not sure why anyone would worry
Wait a second, isn't that the same person that wrote a few days ago that it was something he tried to disable? He even called it a "craplet". For reference, you need to "Change the way Security Center alerts me" first before you turn off/disable the Security Center service, if you don't want the little red shield icon to bug you when Security Center is disabled. I do not personally condone this action, I would much rather see users keep Security Center enabled, notifying them and displaying an icon (the top option).
I noticed one exception in the default firewall configuration that I didn't care for, for allowing remote assistance. I don't think that should be allowed unless you're actually using remote assistance.
I do kind of agree with that, but normally you only use Remote Assistance with users that aren't clever enough to follow your instructions, which usually rules out asking them to modify their firewall so you can take over. In a corporate environment, you'd probably disable that firewall rule and use commercial software (with its own rules) instead to take control.
I certainly wouldn't recommend depending solely on Windows Defender. But it's nice that it's there.
I think that's why it was left in, as people would otherwise question why it's removed, even though it's not perfect, and there are so many reasons why Vista ought to stop something getting onto the user's system anyway. It's like the Malicious Software Removal Tool that Microsoft periodically updates and puts on Windows Update, it's not perfect, it's probably too late, but it makes people happy.
MS has, in a sense, shifted the responsibility onto users
Perhaps that's because they're the problem. Stick an IIS6 box on the web with just port 80 open, and assuming you're only serving static pages (ASP is off by default), that box will never have been compromised between then and now (unless someone knows of an 0-day that I'm not aware of?). Even if you didn't bother installing any patches. Even if you installed ASP, unless someone could upload files to the server and make IIS execute them, you're still not compromised (unless you do something really dodgy in your web application, which typically involves weakening lots of default settings). As a standalone system, Windows is perfectly fine. Once you start putting it on a network, allowing RPC ports to be opened up, exceptions for third party software, using a browser (any browser), that's when the problems start.
Correction I'm grateful to a Reg reader who pointed out an error in a previous edition of this story. I had stated incorrectly that IE7 doesn't allow blocking third-party cookies. It defaults to accepting them, but can be made to block them.
Greene's articles generally need a lot of correcting. Especially his recent ones.
 Yamahito - Wednesday 21st February, 2007 11:45
Yamahito - Wednesday 21st February, 2007 11:45 //In a nutshell, Windows is single-handedly responsible for turning the internet into the toxic shithole of malware that it is today.//
OK, in general I think you over-react to this guy. But they should revoke his Journalism license over that one.
OK, in general I think you over-react to this guy. But they should revoke his Journalism license over that one.
